| Vývojář: | Gate-92 DG (2) | ||
| Cena: | * $11.99 | ||
| Hodnocení: | 0 | ||
| Recenze: | 0 Napsat recenzi | ||
| Seznamy: | 0 + 0 | ||
| Body: | 0 + 0 ¡ | ||
| Windows Store | |||
Popis

Crypto Package Manager (CPM II) is a specialized application for strong encrypting files and folders located on local, networks, servers, or external data media.
The application allows the following actions:
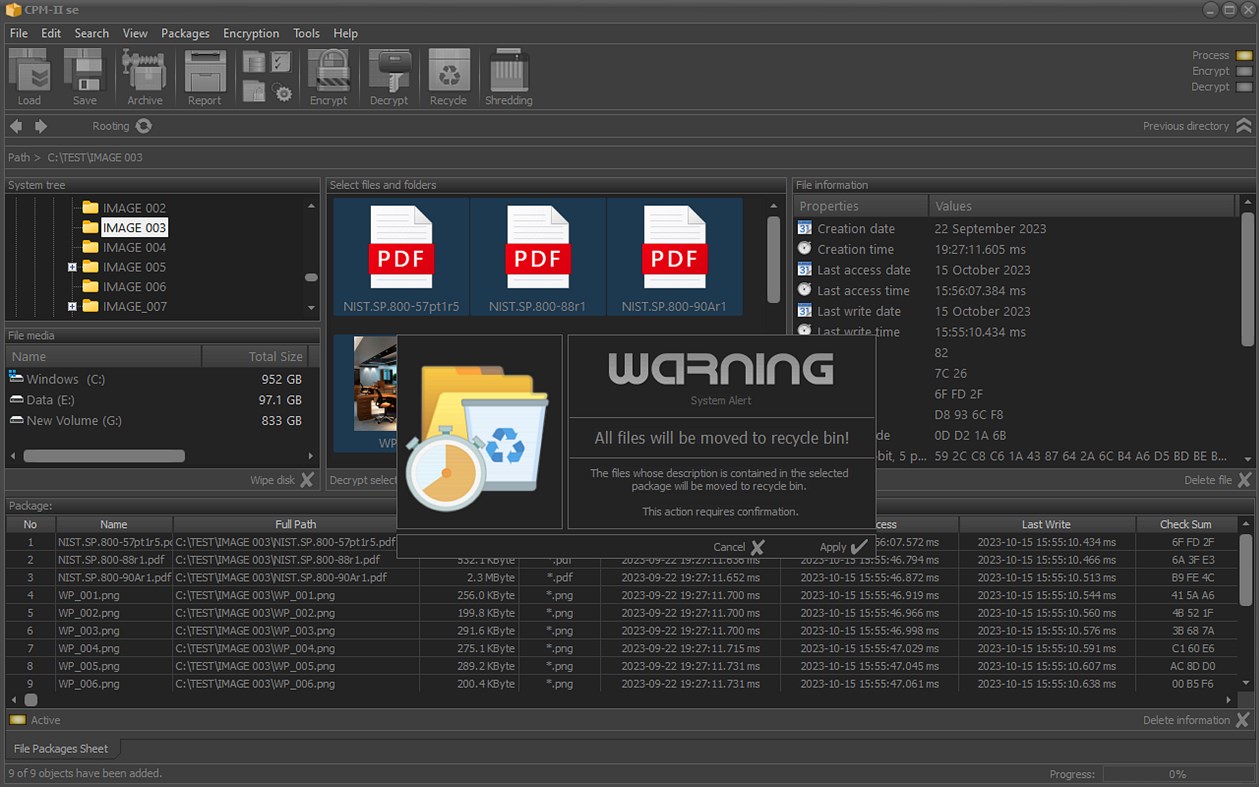
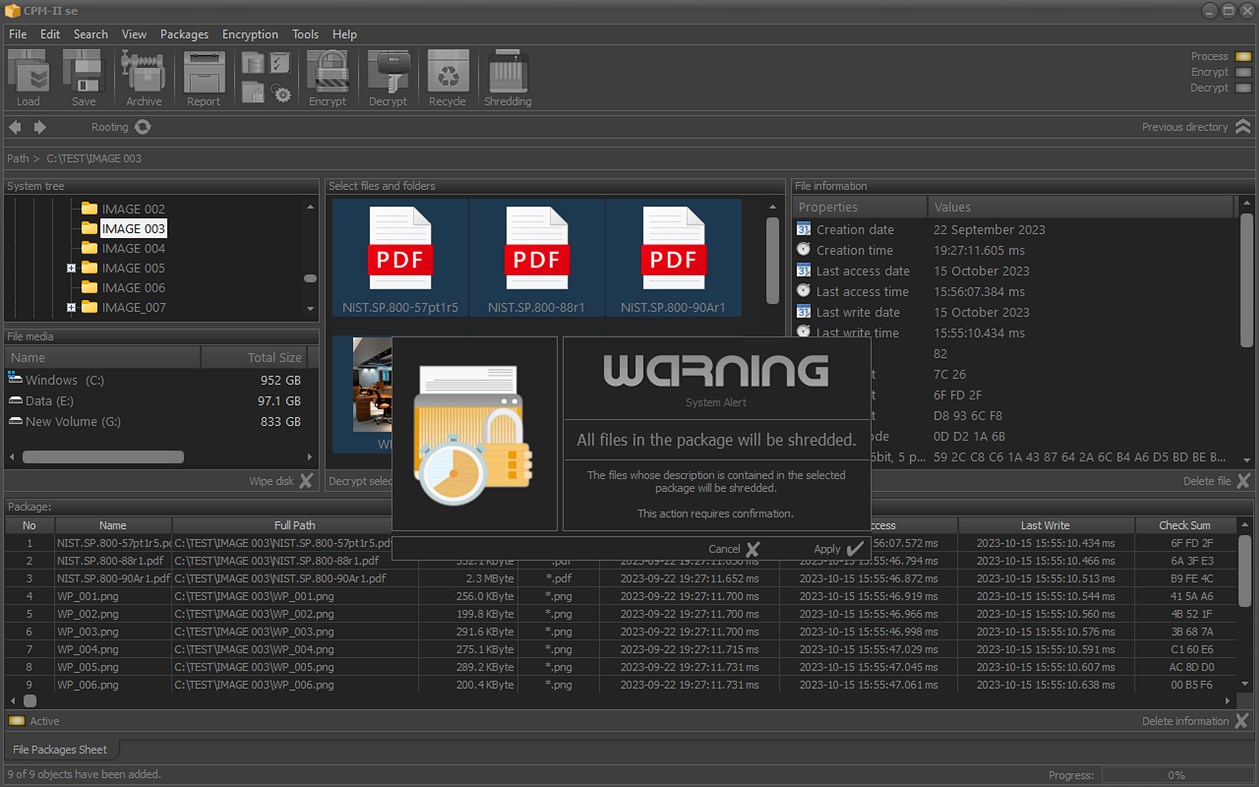
• Encrypt or decrypt selected files and folders;
• Secure file packages;
• Encrypting the files in the package;
• Decrypting the files in the package;
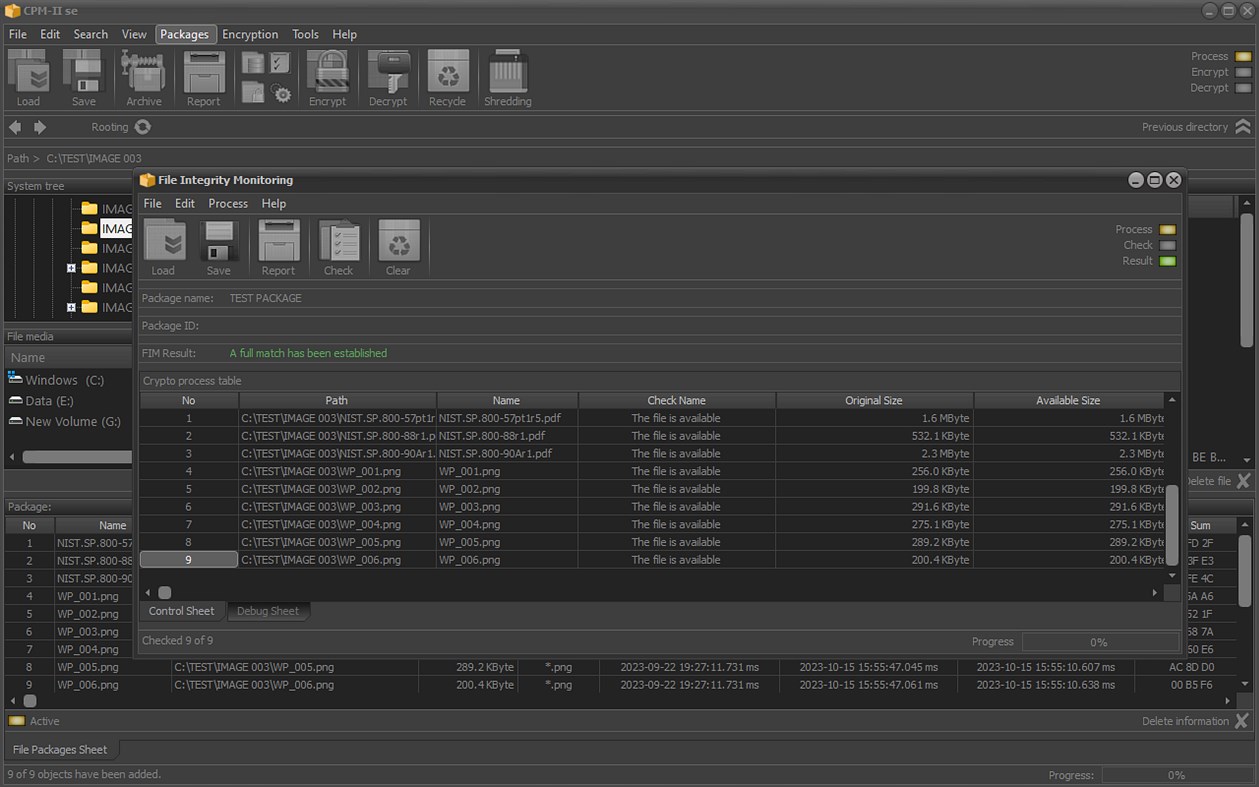
• File integrity check;
• File modification control;
• Checking the current status of files and directories etc.
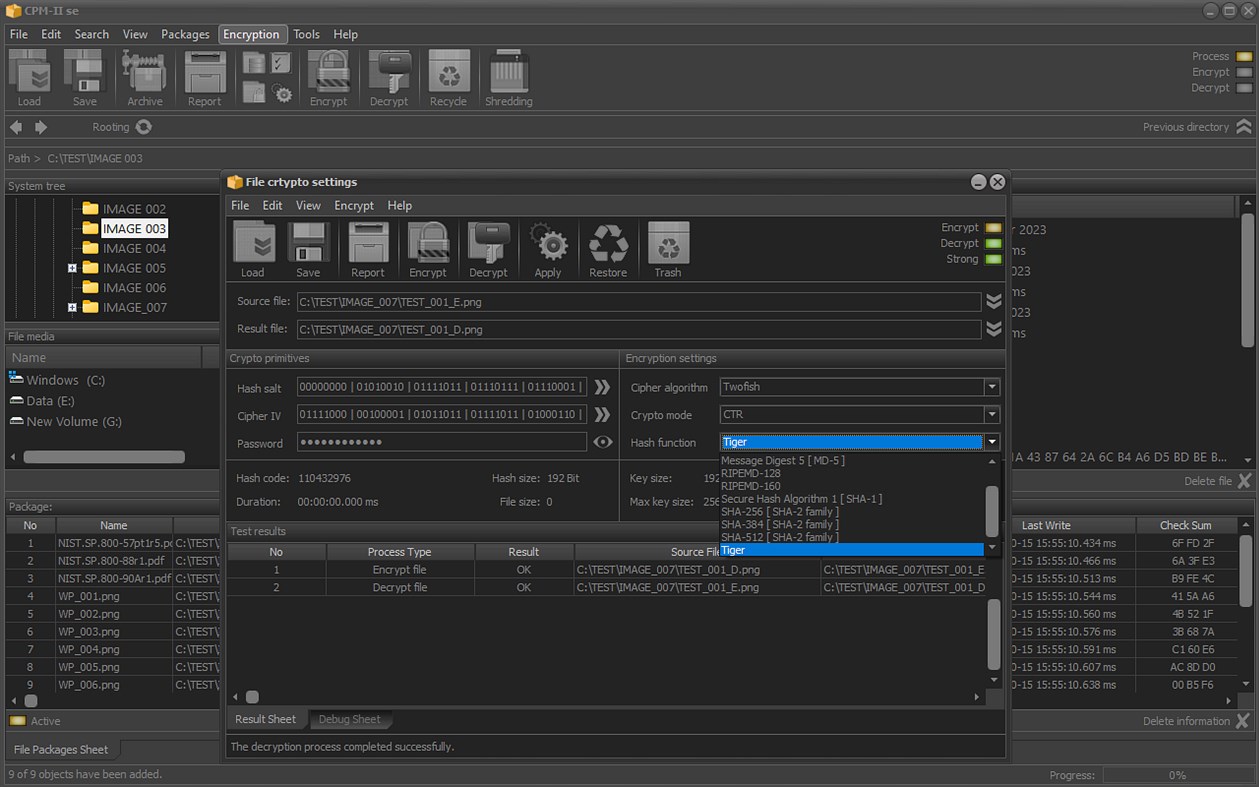
The encryption of the files for which meta-information is available in the packages and which are physically accessible is performed based on session crypto mechanisms.
Each crypto mechanism uses a set of proven cryptographic primitives. Configuration of crypto primitives is done automatically.
All operations on the files and folders saved in the package are performed only when the files and folders are physically accessible. If they cannot be accessed (deleted, physically inaccessible network drive, or other reason), this will be reflected in the packet, recording the time when this finding was made.
FIELD OF APPLICATION
Protecting large arrays of files located on different media is a complex and difficult process to implement. The use of file packages allows the automation of this process, increases the efficiency of service, and significantly improves the security of corporate solutions.
Storing, editing, transferring, and destroying files is a process, the importance of which is often overlooked by both users and those responsible for security.
Statistics show that threats related to gaining unsanctioned access by unauthorized persons are related to this problem.
With the help of CPM, it is possible to neutralize all these problems through a highly effective professional cryptosystem using secure file packages.
CPM uses some of the most effective standard digital data encrypting algorithms used by government organizations and corporate structures.
TECHNOLOGICAL SOLUTIONS
The correct choice of algorithms and software technologies for the encryption of digital data is a guarantee of the high efficiency and reliability of the application.
The application uses a set of standard algorithms to build specialized mechanisms for encrypting digital data.
The following standard algorithms are used in the base version:
STANDARD ENCRYPTION ALGORITHMS
• Advanced Encryption Standard (block size of 128 bits, key lengths: 128, 192, and 256 bits)
• Blowfish
• CAST-128 (CAST-5)
• CAST-256 (CAST-6)
• Information Concealment Engine (ICE)
• Information Concealment Engine 2 (ICE-2)
• ICE Encrypt
• MISTY-1 (Mitsubishi Improved Security Technology)
• Ron's Code 2 or Rivest's Cipher 2 (RC-2)
• Ron's Code 4 or Rivest's Cipher 4 (RC-4)
• Ron's Code 5 or Rivest's Cipher 5 (RC-5)
• Ron's Code 6 or Rivest's Cipher 6 (RC-6)
• Serpent
• Tiny Encryption Algorithm (TEA)
• Twofish
AFFORDABLE HASH FUNCTIONS
• Secure Hash Algorithm 1 [SHA-1]
• RIPEMD-160
• Haval [256 Bit, 5 passes]
• Message Digest 5 [MD-5]
• Message Digest 4 [MD-4]
• Tiger
• RIPEMD-128
• SHA-256 (SHA-2 family)
• SHA-384 (SHA-2 family)
• SHA-512 (SHA-2 family)
USED ISO STANDARDS
• ISO 10116: Information Processing — Modes of Operation for an n-bit block cipher algorithm.
• ISO 9798-2: Information technology — Security techniques — Entity authentication mechanisms — Part 2: Entity authentication using symmetric techniques.
• ISO 10118-2: Information technology — Security techniques — Hash-functions — Part 2: Hash-functions using an n-bit block cipher algorithm.
• ISO 10118-2: Information technology — Security techniques — Hash-functions — Part 2: Hash-functions using an n-bit block cipher algorithm.
• ISO 11770-2: Information technology — Security techniques — Key management — Part 2: Key management mechanisms using symmetric techniques.
USA STANDARDS
• Encryption - Data Encryption Standard (DES) - FIPS 46-3.
• Encryption - DES Modes of Operation - FIPS 81.
• Encryption - Advanced Encryption Standard (AES) - FIPS 197 (with key sizes of 128 and 256 bits).
• Hashing - Advanced Encryption Standard (AES) - FIPS 197 (with key sizes of 128 and 256 bits).
• Guidelines on Electronic - Advanced Encryption Standard (AES) - FIPS 197 (with key sizes of 128 and 256 bits).
LEGISLATION OF USA
• TITLE 50 - WAR AND NATIONAL DEFENSE.
• TITLE 44 - PUBLIC PRINTING AND DOCUMENTS.
• CHAPTER 35 - COORDINATION OF FEDERAL INFORMATION POLICY.
• NSC-63 - PRESIDENTIAL DECISION DIRECTIVE/NSC-63 (PDD-63 1998 г., Hspd-8 2003 г.).
• H.R.145 - 100th Congress (1987-1988).
• NSDD 145 - National Security Decision Directive.
• 10450 - Security requirements for government employees.
• 10501 - Safeguarding official information in the interests of the defense of the United States.
• 10865 - Safeguarding classified information within industry.
• 12829 - National industrial security program.
• 12968 - Access to classified information.
RELATIONSHIP TO GOVERNMENT PUBLISHING
• TITLE 50 - WAR AND NATIONAL DEFENSE.
• TITLE 44 - PUBLIC PRINTING AND DOCUMENTS.
• CHAPTER 35 - COORDINATION OF FEDERAL INFORMATION POLICY.
• NSC-63 - PRESIDENTIAL DECISION DIRECTIVE/NSC-63 (PDD-63 1998 г., Hspd-8 2003 г.).
• H.R.145 - 100th Congress (1987-1988).
• NSDD 145 - National Security Decision Directive.
• 10450 - Security requirements for government employees.
• 10501 - Safeguarding official information in the interests of the defense of the United States.
• 10865 - Safeguarding classified information within the industry.
• 12829 - National industrial security program.
• 12968 - Access to classified information.
RELATIONSHIP TO OTHER NIST DOCUMENTS
( Standards for Security Categorization of Federal Information and Information, FIPS 199 )
• NIST SP 800-60, (Guide for Mapping Types of Information and Information Systems to Security Categories) guides establishing the security categorization for a system’s confidentiality. This categorization will impact the level of assurance an organization should require in making sanitization decisions.
• FIPS 200, (Minimum Security Requirements for Federal Information and Information Systems) sets a base of security requirements that require organizations to have a media sanitization program.
• NIST SP 800-53, (Recommended Security Controls for Federal Information Systems) provides minimum recommended security controls, including sanitization, for Federal systems based on their overall system security categorization.
Snímky obrazovky

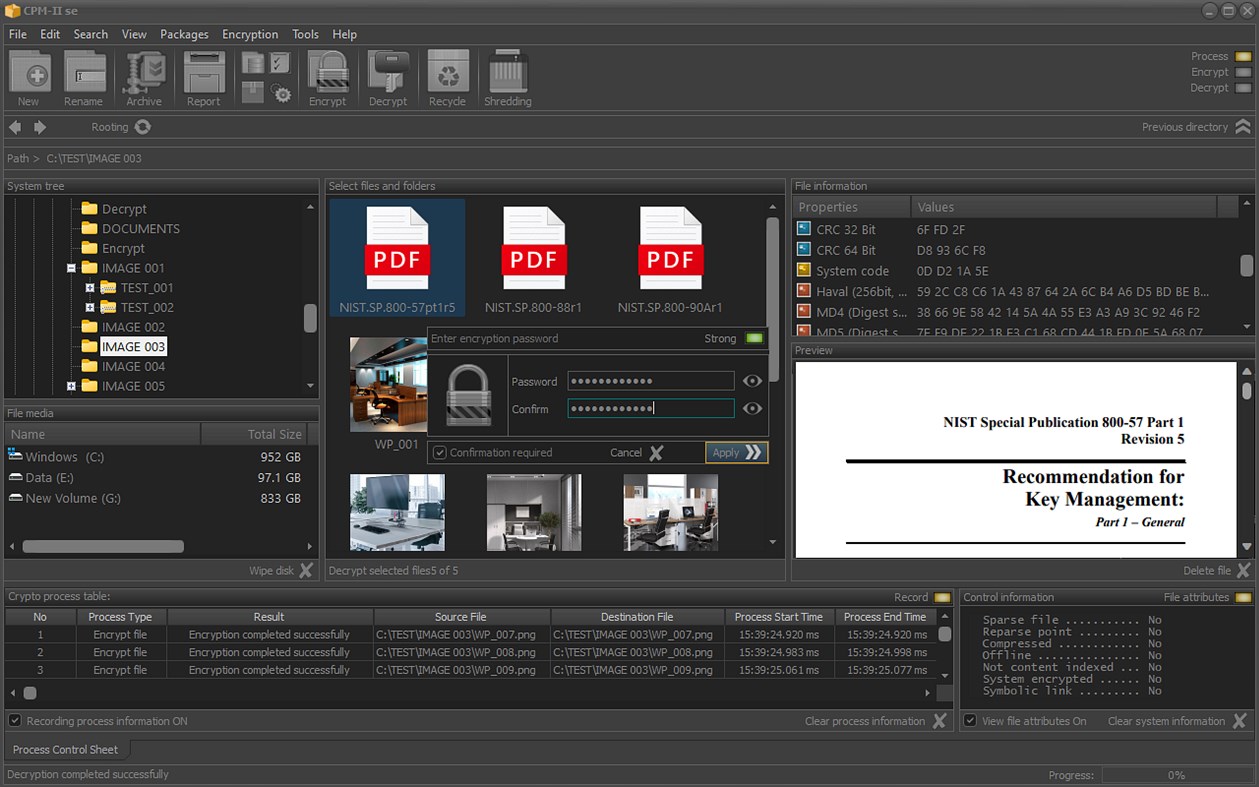
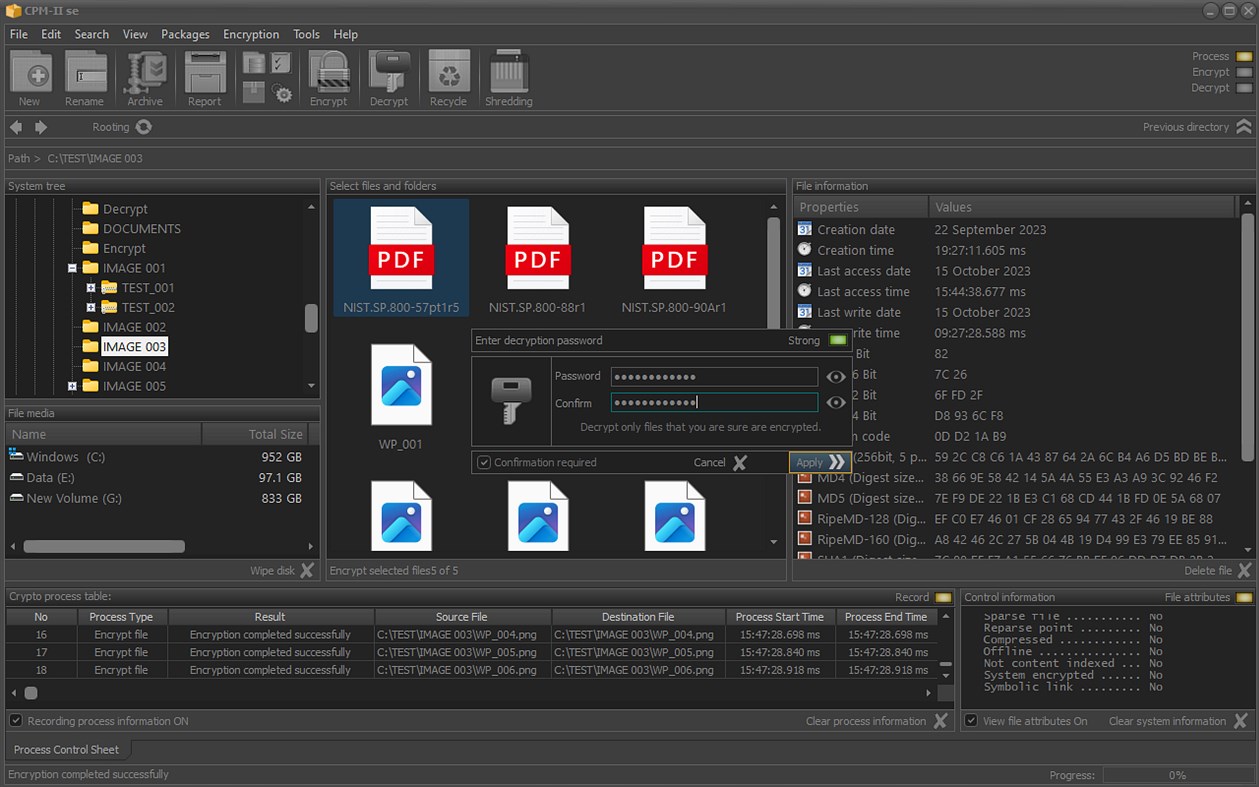
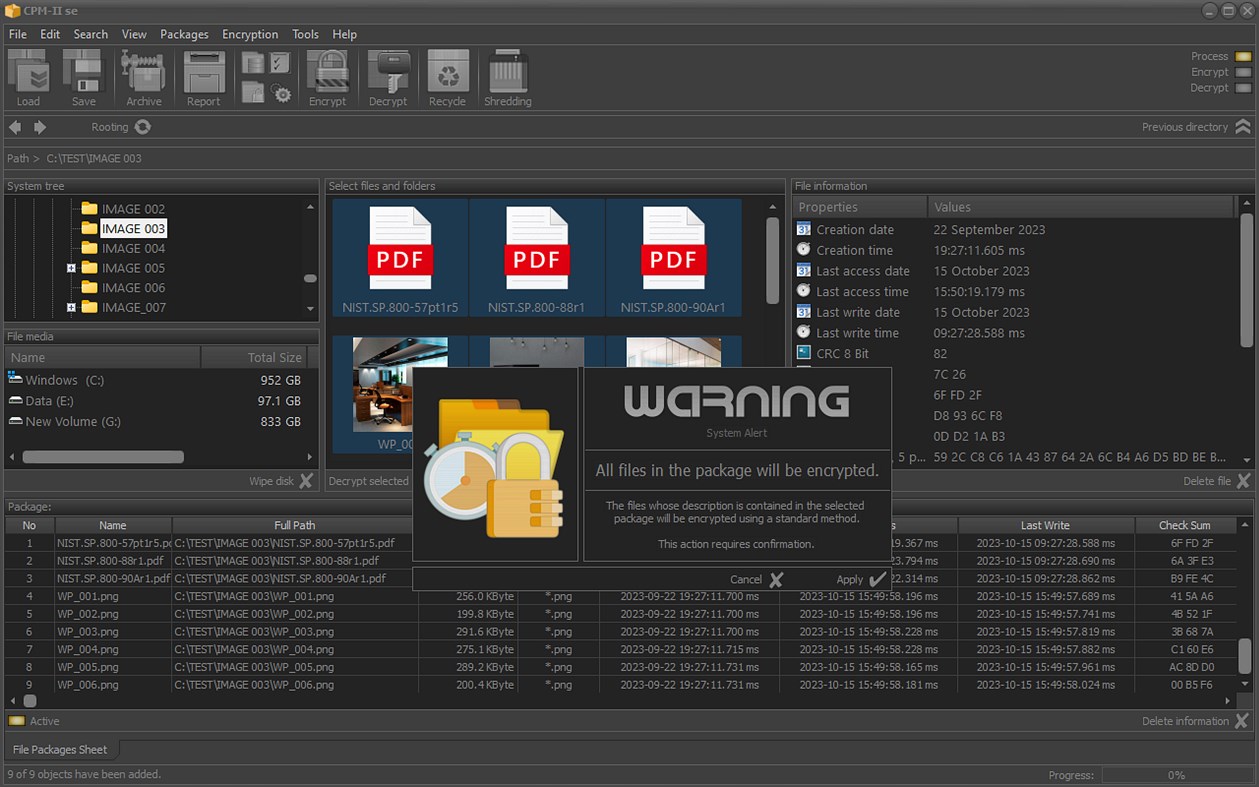
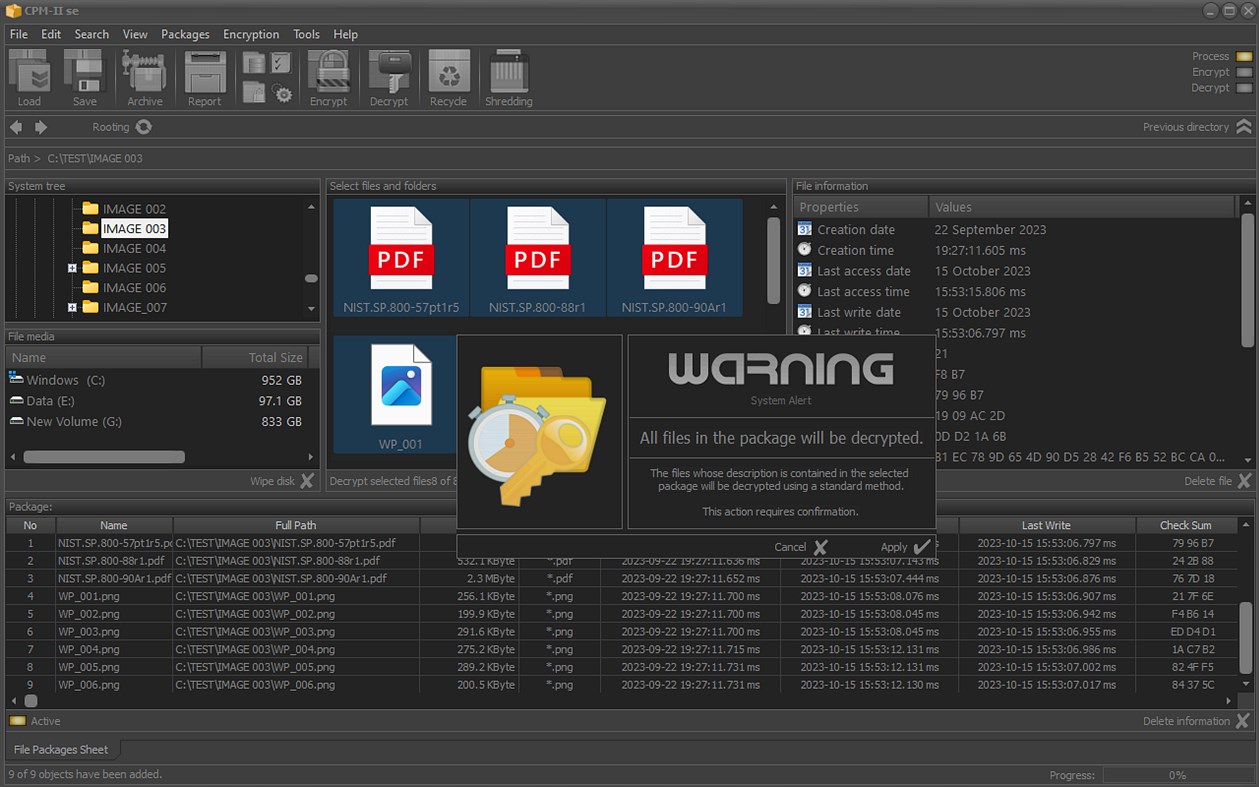
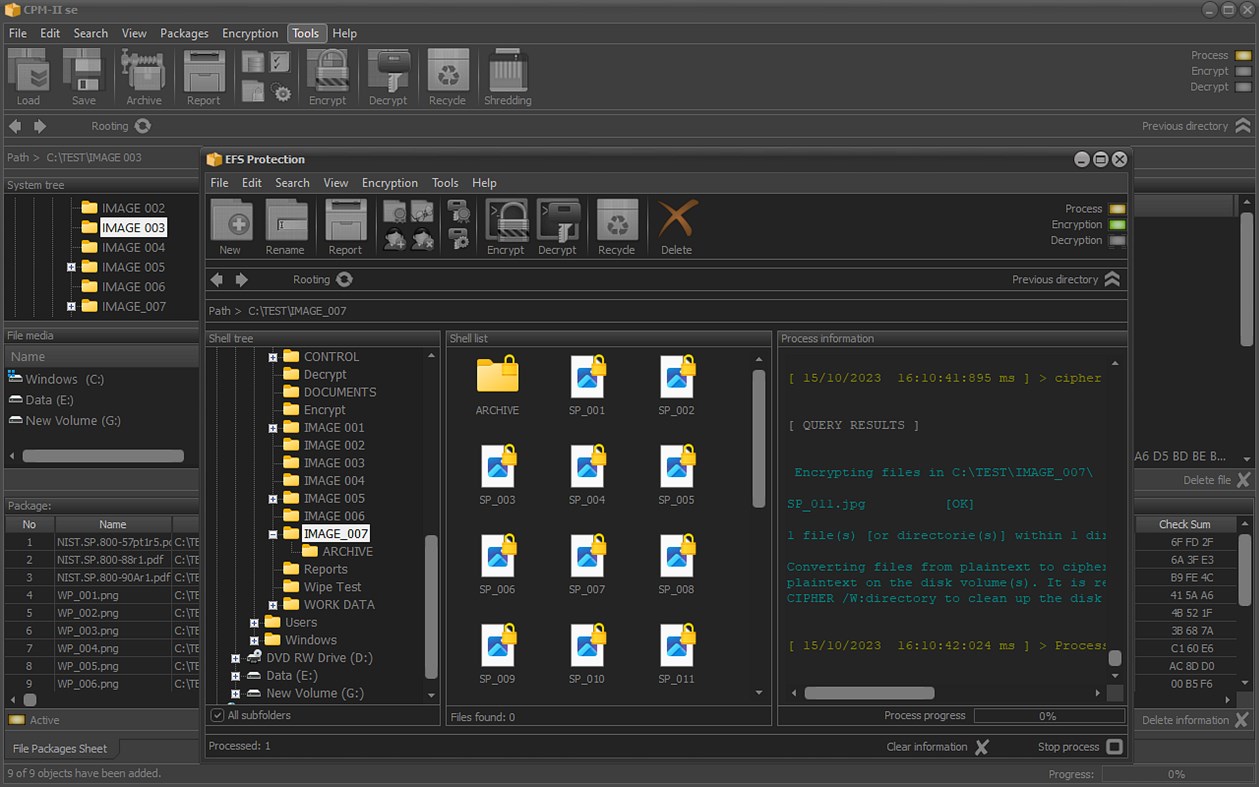
Novinky
- Verze: PC
- Aktualizováno:
Cena
-
* Nákupy v aplikaci - Dnes: $11.99
- Minimální: $4.99
- Maximální: $11.99
Sledovat ceny
Vývojář
- Gate-92 DG
- Platformy: Windows Aplikace (2)
- Seznamy: 0 + 0
- Body: 1 + 2 ¡
- Hodnocení: 0
- Recenze: 0
- Slevy: 0
- Videa: 0
- RSS: Odebírat
Body
0 ☹️
Hodnocení
0 ☹️
Seznamy
0 ☹️
Recenze
Buďte první, kdo bude hodnotit 🌟
Další informace
- Verze: PC
- ID: 9NRL38NNGZCK
- Kategorie:
Windows Aplikace›Zabezpečení - OS:
PC - Velikost:
46 Mb - Podporovaný jazyk:
English - Hodnocení obsahu:
EVERYONE - Windows Store Hodnocení:
0 - Aktualizováno:
- Datum vydání:
Kontakty
Mohlo by se Vám také líbit
-
- CPM II spe
- Windows Aplikace: Zabezpečení Podle: Gatelink Ltd.
- $23.99
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 1 + 0 Verze: PC DEFINITION Crypto Package Manager (CPM II) is a specialized application for professional encrypting files and folders located on local, networks, servers, or external data media. The ... ⥯
-
- SE-02 Explained Course By macProVideo
- Windows Aplikace: Hudba Podle: macProVideo.com
- $9.99
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 0 + 0 Verze: PC Like Master Yoda once said: Size matters not! And like the Jedi Master himself, the Roland SE-02 is indeed very small, but extremely powerful! But you don't need to learn to use the ... ⥯
-
- MultiCommander SE (Store Edition)
- Windows Aplikace: Pomůcky a nástroje Podle: Mathias Svensson
- Zdarma
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 0 + 6 (4.2) Verze: PC Multi Commander is a multi-tabbed file manager and is an alternative to the standard Windows Explorer. It uses the very popular and efficient dual-panel layout. Multi Commander has ... ⥯
-
- Corel PaintShop Pro 2019 SE
- Windows Aplikace: Fotky a videa Podle: Corel Corporation
- Zdarma
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 0 + 0 Verze: PC Experience a professional photo editor designed by the passionate photo enthusiasts who use it. PaintShop® Pro 2019 is your affordable, user-centric alternative to Photoshop with every ⥯
-
- RWE SmartHome
- Windows Aplikace: Byznys Podle: RWE International SE
- Zdarma
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 0 + 1 (3.0) Verze: PC The app offers convenient access to your RWE SmartHome system. When log in for the first time, the log-in data can be saved in the settings and will then be available every time you ... ⥯
-
- SAP Fiori Client
- Windows Aplikace: Byznys Podle: SAP SE
- Zdarma
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 0 + 15 (4.4) Verze: PC The SAP Fiori Client mobile app for Windows is an enhanced mobile runtime for the more than 1,100 SAP Fiori apps that can increase your productivity by tackling your most common daily ... ⥯
-
- Recipe Cookbook Manager
- Windows Aplikace: Jídlo a stravování Podle: Wes.SE
- Zdarma
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 0 + 1 (1.0) Verze: PC This app allows you to easily track your favorite recipes. In the future, it will also allow you to manage and export shopping lists so you never have to worry about being unprepared ... ⥯
-
- BIMx Desktop
- Windows Aplikace: Produktivita Podle: Graphisoft SE
- Zdarma
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 0 + 0 Verze: PC Graphisoft s BIMx Desktop is an interactive app for exploring BIM projects and linked documentation sets created in Archicad and DDScad and enables viewers to explore architectural ... ⥯
-
- Rosetta SIE-XBRL/GL Viewer
- Windows Aplikace: Byznys Podle: Alphabet AB
- Zdarma
- Seznamy: 0 + 1 Hodnocení: 0 Recenze: 0
- Body: 1 + 2 (4.5) Verze: PC Read and analyse bookkeeping files, from email, on the desktop and over internet! Rosetta presents financial reports from standard SIE, XBRL/GL and Rosetta accounting files! It exports ⥯
-
- Vision Business Calculators
- Windows Aplikace: Byznys Podle: Vision App Development UK
- Zdarma
- Seznamy: 0 + 1 Hodnocení: 0 Recenze: 0
- Body: 1 + 1 (5.0) Verze: PC Vision Business Calculators (Powered by OMNI) are powerful business calculators that can be used for all your business needs and is a great app for working out everything from break ... ⥯
-
- Verifiquese Cedula
- Windows Aplikace: Byznys Podle: Venko SAS
- Zdarma
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 0 + 0 Verze: PC Verifíquese Cédula Beta es una aplicación que permite acceder a información publicada en internet asociada a la cédula de ciudadanía Colombiana de una forma sencilla y en un solo ... ⥯
-
- The Operator
- Windows Aplikace: Produktivita Podle: Datatal
- Zdarma
- Seznamy: 0 + 0 Hodnocení: 0 Recenze: 0
- Body: 0 + 1 (5.0) Verze: PC Presentity Telefonist is a modern and effective tool for the company switchboard to answer, search, and route calls from your computer. The operator is an additional function to the ... ⥯